ABSTRACT
In this poster we present a
platform-based approach to the PKI integration. The platform provides a
standardized uniform access to the public key services and allows integration
with arbitrary PKI implementations. Besides interacting with a PKI the platform
also provides authentication and authorization services to the participating
applications.
Keywords
Security, PKI, integration, public
key services, abstraction frameworks, authentication, authorization
1. INTRODUCTION
Public Key Infrastructure (PKI)
plays an important role in securing web-based communications in general and Web
Services in particular. A vivid example of the PKI importance is the dominant
use of the SSL/TLS protocol [1] for providing secure communications between web
clients and servers. The advent of Web Services makes PKI even more important
since persistent privacy and integrity of the SOAP messages, governed by the
WS-Security specification [4], is based on the XML-DSIG [2] and XML-ENC [3]
standards that engage public key cryptography.
Early simple PKI deployments [5,
6] assumed only one source of digital certificates. Today_s more robust PKI
infrastructures, such as those required by Web Services, have to deal with
multiple sources of digital certificates and manage complex bridged trust
chains [7]. The environment becomes even more complex with the introduction of
spanning PKIs that host multiple certificate authorities [8]. The growing
complexity of the PKI in use and the abundance of the PKI implementations makes
it practically impossible for Web Services to address issues related to
validating and locally storing certificates, calling for an abstraction layer
that insulates Web Service from the varying requirements of different PKI
services providers.
2.INTERMEDIARY
SECURITY FRAMEWORK
In this poster we present a common
Intermediary Security Framework (iSF) that provides security infrastructure
components rendering authentication, authorization, and PKI storage and
verification services to the Web applications. iSF provides an abstraction
layer that insulates applications from the authentication and authorization
Enterprise Security System (ESS) and the deployed PKI solution, thus presenting
a monolithic view of the security infrastructure. At the same time, iSF allows
applications to use the existing Enterprise security infrastructure and PKI
more easily, and makes possible orderly and secure transitions between
different security domains and simplifies complex PKI related functions.
The framework exposes to a Web Service or any other
application a simple but sufficient interface for accessing certificate stores
and verifying validity of peer certificates. The framework delegates actual
interaction with diverse PKI systems to a dedicated service, called the
Intermediary Security Service (iS2). iSF architecture related to the PKI
services is presented on Fig. 1.
The application side of the framework transparently interacts with iS2 using the XKMS protocol [9]. XKMS specifies two sub-protocols for distributing and registering public keys: the XML Key Information Service Specification (X-KISS) and the XML Key Registration Service Specification (X-KRSS). The X-KISS specification defines a protocol for a trust service that resolves public key information and the X-KRSS specification defines a protocol for a web service that accepts registration of public key information.
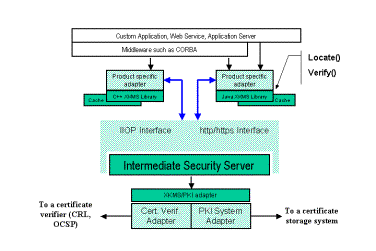
Figure 1 Intermediate Security
Framework (iSF) PKI components
iSF implements the X-KISS part of the XKMS protocol.
iSF clients access PKI public key services abstracted by the framework using
two basic methods: Locate and Verify. The Locate method allows iSF client to
request required certificates or certificate sets. The Verify method provides
certificate validation services such as, but not limited to, CRL checks and
online certificate verification via the OCSP protocol [10]. iSF clients are
unaware of which PKI solution is deployed or even that the XKMS protocol is
used: results of the client_s query are communicated to the client in a simple
data object which methods the client later invokes to extract the required
information.
On the client side the XKMS protocol implementation
is wrapped into a simple PKIService interface which exposes two methods: locate
(_) and validate (_). Each of these
methods takes a desired public key designator and a list of requested
parameters and returns an object of the PKIObject type which properties can be
interrogated to determine certain characteristics of the public key in question
such as its usage.
As shown on Fig.1, XKMS requests are delivered to
iS2 over the http(s) or the iiop(s) protocol. Communication between iS2 and the
deployed PKI systems is provided via dedicated adapters. Upon receiving an XKMS
request iS2 dispatches it to an appropriate adapter. The standard adapter layer
translates an XKMS request into an internal binary representation and invokes a
dedicated portion of the adapter, called the PKI system adapter.
The PKI system adapter is the only element in the
framework aware of the real deployed PKI and its specific properties. A PKI
system adapter may interact with more than one PKI system at once in order to
fulfill the client_s request. The PKI system adapter passes the result back to
the standard layer which formats an equivalent XKMS response and passes it back
to the client via the iS2 service. The iS2 service optionally caches results of
the queries. This cache is valid for a certain period of time determined by the
system administrator.
In order to increase the performance even further, results of the client_s XKMS queries can be optionally stored in a local cache on the client. Same as the iS2 cache, this cache is valid for a certain period of time also determined by the system administrator. iSF client may query iS2 to determine the latter cache validity period and adjust its own setup according to a rule provided by the system administrator.
3. CONCLUSION
Integrating various security solutions is a hard problem and was considered almost intractable for a long time. With the advent of new basic standards for passing security information, such as OASIS SAML and XACML, W3C XKMS, etc., a new class of security frameworks, often referred to as Enterprise Application Security Integration (EASI) solutions, addresses the problem of extending security protection across the Enterprise. These frameworks address two important aspects of security integration: they allow integrating applications into the existing Enterprise wide security solutions, and provide a basis for integrating different security solutions deployed at the Enterprise. This latter capability is extremely important for large enterprises, where there_s no such thing as a _one size fits all_ approach. In such systems, multiple security solutions are typically deployed over time due to factors such as cost, mergers and acquisitions, and advances in technology.
Intermediate Security Framework (iSF) proposed in
this poster is a robust and efficient method of providing authentication,
authorization and certificate storage and verification services to the Web
based applications. iSF abstracts its clients from the details of the immediate
security system or a PKI system in use.
The PKI component of the
Intermediary Security Framework described in this poster session is being
implemented in IONA Application Service Platform 6.1.
REFERENCES:
1.
T.Dierks, C.Allen, The TLS Protocol, IETF RFC 2246, 1999
2.
D.Eastlake, et al, XML-Signature Syntax And Processing, IETF
RFC 3275, 2002
3.
D. Eastlate, J. Reagle (editors), XML-Encryption Syntax And
Processing, http://www.w3.org/TR/xmlenc-core/, 2002
4.
Phillip Hallam-Baker, et al (editors), Web Services Security
Core Specification, OASIS, 2002
5.
C. Adams, et al, Understanding The Public Key
Infrastructure: Concepts, Standards And Deployment Considerations, New Riders
Publishing, 1999
6.
A. Nash, et al, PKI: Implementing & Managing E-Security,
McGraw Hill Osborne Media, 2001
7.
NIST PKI Program, http://csrc.nist.gov
8.
Ken Klingenstein, PKI: News From The Front And Views From
The Back, Internet2 Project, 2002
9.
Phillip Hallam-Baker (editor), XML Key Management
Specification (XKMS 2.0), http://www.w3.org/TR/xkms2/,
2002
10.
M.Myers et al, X.509 Internet Public Key Infrastructure
Online Certificate Status Protocol _ OCSP, IETF RFC 2560, 1999