ABSTRACT
By the use of declarative rules, automation of tasks can be
performed through an electronic personal information management (PIM)
application. Rules can be used in a variety of different scenarios, for
instance to trigger information retrieval tasks or to send out notifications
when a pre-determined set of conditions are satisfied. The technology described
is an integral part of the IBM Tempus Fugit [1] research project.
Keywords
PIM, Rule Engines, Java, XML, Messaging, Information Retrieval, AI
1. INTRODUCTION
Several technologies have made it possible for personal information management applications to become “smarter? First of all, emerging groupware standards simplifies access to PIM data on heterogeneous systems, enabling effective exchange of schedules, address books, todo items etc. Secondly, “intelligent? PIM applications can utilize emerging services infrastructures [2] to associate active, context sensitive information such as flight schedules or weather forecasts with scheduled activities.
However, applications that are able to provide the “right information at the right time? and perform automated tasks on behalf of users need to be guided by a specific set of rules. A forward chaining inference rule engine provides a solution that can be used in a variety of different circumstances.
2. ARCHITECTURE AND IMPLEMENTATION

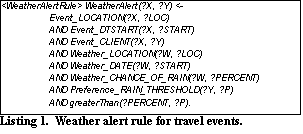
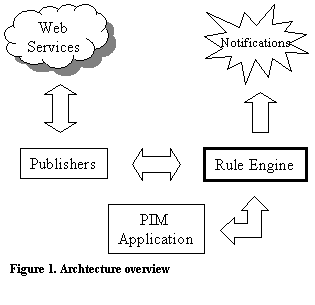
Figure 1 shows an architecture overview. Information entered into a PIM
application is forwarded to a rule engine, which transforms the information
into knowledge (facts). Publishers provide the next step in the chain by
periodically querying services on the Web for relevant context sensitive
information, incorporating the results into the rule engine knowledge
base. Configuration of the
publishers is dynamically handled by rules triggering on various application
events, such as the scheduling of a new meeting in a calendar. By attaching procedures to the derived
conclusions (also called effectors, see [3]), tasks can dynamically be
performed.
Listing 1 shows an example of how a Weather alert rule is described using Courteous Logic Programs (CLP) [3]. The rule fires if the chance of rain at the destination for a scheduled travel event is higher than user-specified threshold. If a “send-email?procedure is attached to the rule, users will automatically be notified whenever bad weather is forecasted. Facts are represented using an identifier for the type of object described, followed by ‘_?and the name of a particular attribute. For example, ?i>Event_DTSTART? indicates the start date of a scheduled calendar event. Attributes associated with calendar PIM objects comply with the iCalendar [4] naming conventions. The predicates are 2-ary, where the first function symbol contains the unique key for the object instance, and the second contains the value for the attribute described. The Weather facts has been created by a weather publisher that periodically accesses online weather services to retrieve the latest weather data.
2.1 Implementation
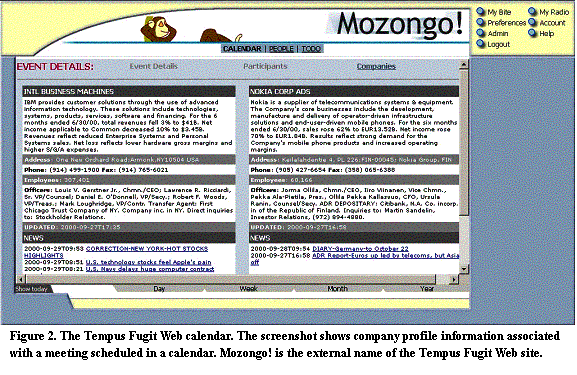
Tempus Fugit is a Web based electronic calendar hosted on an application server (see screenshots in Figure 2). The system provides the traditional PIM functionalities, such as calendaring and email, but also has the ability to tie in additional context sensitive information and provide the users with such information “just-in-time? In the current implementation, the system is able to provide company profile information, including recent company news, and attaches such information with scheduled company visits in a calendar. The news items are also sent out via email starting a couple of days before the scheduled event, so that the users can be properly “briefed?about their upcoming visit.
Tempus Fugit also uses rules to send out notifications to meeting attendees at scheduling time, giving attendees the ability to respond to invitations. Other uses of the rules is for performing system administration tasks, for instance deleting expired information or sending out notifications to the administrators reporting user activities. Rule authors can relatively easily implement new features and support new requirements by adding rules or modifying existing rules
3. FUTURE DIRECTIONS
An overview has been given of how rules and rule engines can successfully be integrated into a personal information management system or groupware application. There is much to be gained by externalizing parts of the application logic into rules, for instance the possibility of automating tasks that traditionally have been taken care of by agent based technologies. The Tempus Fugit research project is continuing to investigate these technologies, with the goal of one day automating and supporting many of the tedious tasks that people face daily.
 |
4. ACKNOWLEDGMENTS
I would like to thank the people in my group who has helped out the project, including Daniel Ford, Joann Ruvolo, Jussi Myllymaki, James Kaufman, Martin Gerlach, Steffen Lassahn, Jared Jackson and Norm Pass.
5. REFERENCES
[1] D.
Ford et al., “Tempus Fugit: A system for user automation and awareness?
(Submitted)
[2] Simple Object Access
Protocol (SOAP) 1.1 http://www.w3.org/TR/SOAP
[3] Benjamin N.Grosof. “Courteous logic programs: Prioritized conflict handling for rules.? Technical report, IBM T.J. Watson Research Center, http://www.research.ibm.com, search for Research Reports. P.O. Box 704, Yorktown Heights, NY 10598. Dec. 1997. IBM Research Report RC 20836. Library of Congress. LC Classification Outline, fifth edition. 1986.
[4] Internet Calendaring and Scheduling Core Object Specification. http://www.ietf.org/rfc/rfc2445.txt